Research Article: 2020 Vol: 24 Issue: 2
Use of Cloud-Based Accounting Technologies in The Information Security System
Liudmyla Sokolenko, Sumy State Pedagogical University named A. S. Makarenko, Ukraine
Tatyana Egorushkina, Plekhanov Russian University of Economics, Russia
Olha Kosytsia, Kharkiv National University of Internal Affairs, Ukraine
Oleksandr Atamas, Dnipro State Agratina Economic University, Ukraine
Olha Kyiashko, Kyiv National University of trade and economics, Ukraine
Abstract
The existing standards in the field of creation of cloud information-and-computing systems were studied, main issues related to the use of cloud technologies were determined. The models of architectural levels of the computing cloud spread in the world were considered, and their advantages and disadvantages were determined. Their characteristics were compared with the indication of the degrees of implementation and functional capabilities. The international standards have mainly conceptual-recommendation nature and do not take into account main factors, which significantly influence the accuracy and objectivity of risk evaluation. When introducing cloud technologies, one should have a strategic plan that will help to correctly set goals and see their achievement, control and coordinate the movement to the result achievement. The issue of the development of IT-strategy of introduction is in that it is important to determine, as early as at the stage of its formation, which models of formation of risks of data loss will satisfy the corporation when transferring to the cloud environment, evaluate providers of cloud services in terms of reliability and safety. The paper describes aspects of use of cloud technologies in accounting, the analysis of their application in the world practice and by business has been performed. The substantial attention has been paid to the characteristics of advantages and disadvantages of use of cloud technologies in business and accounting, in particular.
Keywords
Cloud Computing, Information Technologies, Digitation of Reporting, Analytic Hierarchy Process, Information Safety.
JEL Classifications
M5, Q2
Introduction
The cloud technologies are of interest for both large companies that try to optimize their expenses for IT-infrastructure of the corporation, and small companies, which have no capability to immediately deploy their own infrastructure. The growing of interest to the technology of cloud computing is related to the economic effect of their use. However, despite of the clear benefits, it is necessary to solve a number of issues, when using cloud computing. The main of them are the trust to the service provider, provision of confidentiality, integrity, authenticity and inconsistency of information at all stages of its existence, uninterrupted operation, protection against unauthorized access and storage of personal data of users that are transmitted and processed in the cloud.
Accounting as a branch of enterprise management activities related to the regular implementation of algorithms for collecting, storing and processing information on business activities has all the prerequisites for the implementation of modern information technologies in order to automate operations.
The impetus to the rapid development of cloud technologies was the implementation of connection of various devices to the global network, so called Internet of Things - IoT).
The growing number of connections of mobile devices to the Internet using social networks and cloud infrastructure for solving various tasks is characterized as Third platform.
The clouds are often compared with mainframes. The difference between the cloud and mainframes is in the limitedness (theoretically) of its calculation capacity, as well as interaction of a user with a task sent for processing.
The internet-services of e-mail, office applications, graphical editors, music and video services, online TV became usual for average citizen long now. All these are elements of “cloud” technologies that are rapidly developed today. These technologies are actively entering the life of modern business, automate many of its daily tasks, including accounting maintenance. Many offers related to the introduction of these technologies in the business practice occurred in the market of the accounting software. The leading developers of accounting programs declare capability of integration on new versions of programs with technologies of cloud computing.
Review of Previous Studies
The essence of the cloud computing is to provide the end users with the remote dynamic access to the services, computing resources and applications (including operation systems and infractructure) via Internet (Drobyazko et al., 2019a, b).
The development of the hosting area was caused by the need in software and digital services, which could be managed from inside, but which would be more saving and efficient due to the scale (Linthicum, 2017).
The urgent task that involves the theoretical-methodological justification of the impact of information technologies on the state and methodology of accounting, updating of its subject, method, functions and purpose needs to be solved in terms of science Hilorme et. al. (2019a), Hilorme, (2019b). The aspects of development of methodological approaches in the context of development of the strategy of building of accounting on the basis of the introduction of ERP technology, formation of the complex managerial information system, and justification of the organizational-economic areas of state regulation of accounting in the conditions of management digitalization require substantial analysis.
The new area of scientific research in accounting is the justification of the theoretical-methodological principles of accounting in the conditions of digitalization.
Digitalization is the transfer of the information field to the digital technologies, that is conversion of certain information in digital format to ease its further use on modern electronic devices (Mangiuc, 2017; Stancheva-Todorova, 2018; Stancheva-Todorova, 2019; Neovius & Duncan, 2017).
As information technologies develop, the irrepressible wave of digitalization is continuosly moves forward penetrating various areas of our life, and accumulates on all things, which it manages to “touch” (Marshall & Lambert, 2018).
The significant part of equipment that surrounds us is automated already and capable perform a massive number of tasks independently without human intervention to collect data, analyse them and return certain algorithms that allow even make accurate forecasts for the future (Woodside et al., 2017).
Despite the fact that such tendencies are an indicator of modern development of social-economical relationships, but in the context of automation of accounting, the matter of digitalization is unstudied and need in both theoretical justification and methodological support.
Despite the obvious benefits, there is huge number of myths around the cloud services. The users most ofter consern the matter of the reliability of data protection in a cloud. According to the results of survey conducted by Ipsos on the order of Microsoft, 91% of companies that do not use cloud services yet noted that the issue of data safety in a cloud is their largest consern. However, the high reliability and safety became the basic reason of choice of cloud services among Ukrainian companies that already migrated to a cloud, as stated by 90% of current users.
Methodology
The SAP system developers proposed the special system of ERP (Enterprise Resource Planning) modules that control, improve and simplify work at all sites of business: from entering information from primary trade-accounting registrars to the management of support of making strategically important decisions.
Based on this software and indicators collected by it, the enterprise creates unified information space that is structurally divided by hierarchical levels and areas of work - sale, procurement, production planning, operational activities, financial and warehouse accounting, etc., which allows to cover absolutely all areas. All information is accumulated and entered into a unified database, from where it can be easily getting upon request.
Results and Discussion
The issue of the information safety, when using cloud computing for small and medium-sized enterprises processing their own information is not too critical. Quite different is the case with large companies or companies that need to strictly adhere to regulatory documents in the field of information safety, such as government agencies, financial institutions, medical institutions, personal data operators, etc. At present, this is indeed one of the main factors that hinder the provision of cloud services to organizations that handle restricted information.
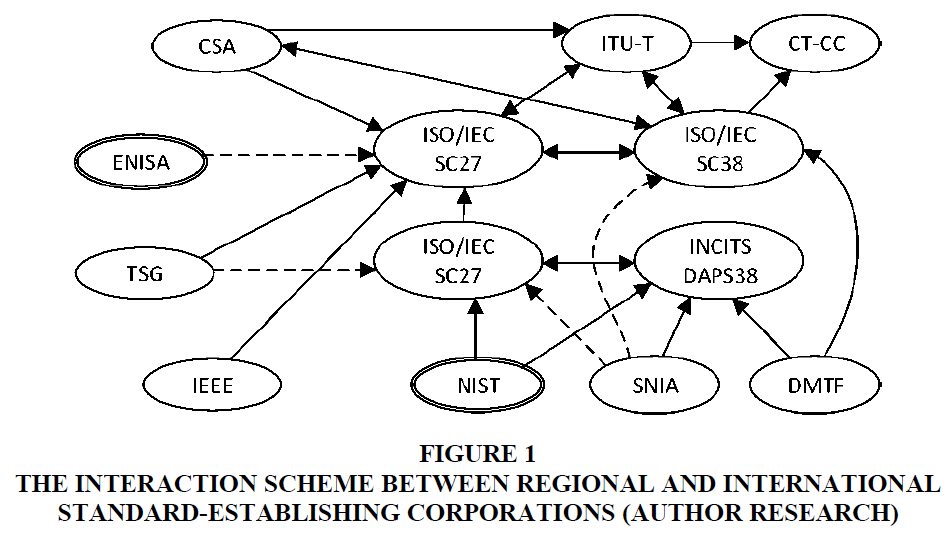
According to the existing classification, the standard-establishing corporations and bodies have the following hierarchy of levels: International (ISO / IEC, ITU); Interstate (forums and consortiums); Regional (European CEN/CENELEC); National (state laws and standards, departmental normative documents, manuals, instructions, etc.).
For the standardization of cloud technologies state borders move back, since service providers are mainly located in different countries and continents.
Because of absence of international standards on certification of elements of the cloud infrastructure and urgency of the information safety, the elements (data-centers, channels and communication networks, and others) use certificates of safety of standards both international ones and other countries, and adjacent areas.
Figure 1 shows the diagram of interaction of international and regional standard-establishing corporations in the area of cloud technologies.
Figure 1 The Interaction Scheme Between Regional and International Standard-Establishing Corporations (Author Research)
The cloud technologies allow to give to the users the accounting and managerial systems, corporate e-mail, and document flow as the Internet-service. The accountants use the cloud services for long time. They include: client banks, e-mail, program of delivery of accounting reporting. Now there is a turn for accounting programs.
The creation of a unified cloud computing risk assessment technique is hampered by the lack of a single, standard, structured platform that could help corporations assess and mitigate cloud technology risks. So, there are methods in place to make the system secure initially, rather than using the security certificates of a cloud service provider.
The feature of management decisions is the need to take into account the influence of uncertain factors and to consider all possible consequences and alternatives.
The development of decision models under uncertainty is of great practical importance.
A major threat to the performance of a corporation is a breach of the information integrity.
Currently, there is an increasing number of threats and vulnerabilities of information such as fraud, espionage, vandalism, fire or flood. Risk assessment is an important part of determination of the scale and likelihood of information security threats.
In the process of risk assessment, the following is assessed: the likelihood and potential loss from the identified threats, measures of the level of risk of information assets, and also relate them to confidentiality, integrity and accessibility; the effectiveness of existing measures to identify the most critical assets of the corporation and identify priorities and recommendations for asset protection.
According to the Facilitated Risk Analysis Process (FRAP), risk assessment is carried out for an unsecured ICT system, which allows to show the effect of the implementation of the information security system (ISS).
The evaluation is based on the following indicators.
Probability: High Probability - it is very likely that the threat will be implemented in the next year; Medium Probability - the threat may be implemented in the next year; Low Probability - it is unlikely that the threat will be implemented in the next year.
Impact - a measure of the loss or damage to an asset: Impact - stopping of critical processes, which leads to significant losses, loss of image or loss of significant profit; Medium Impact - short-term interruption of critical processes; Low Impact - a break in work that does not cause significant financial losses.
The evaluation is determined according to the rule given by the risk matrix (Table 1).
| Table 1 Information Risk Matrix According to Frap Method with the Implementation of Cloud Technologies (Author's Development) | ||||
| LOSS | ||||
| High | Medium | Low | ||
| Probability | High | A | ? | ? |
| Medium | ? | ? | ? | |
| Low | ? | ? | ? | |
Decisions related to the migration of enterprise applications to the cloud can be considered strategic, since they are associated with significant costs of different resources and a large amount of uncertainty in the decision-making environment, which have long-term consequences for the corporation.
After selection of cloud-based IT services that are effective for introduction in the corporation, you need to compare them with each other. This will allow to identify the most suitable services for working in a cloud environment.
To support decision-making on the migration of corporate applications to the cloud environment, the following model is proposed to evaluate the applications that are used in terms of their suitability for cloud operations.
This approach has a multidimensional expert evaluation. Corporate applications are proposed to be evaluated by three group criteria:
1. Business value. What business value can a corporation gain by moving applications to the cloud?
2. Technical capability. Is it realistic to migration applications to the cloud?
3. The degree of risk. What is the risk of migration of applications to the cloud?
Each of these criteria is critical to making a positive or negative decision to migrate applications to the cloud. For example, an application may be highly valued in terms of business value and technical capability, but may not be a good candidate for cloud transfer if the level of risk exceeds the risk acceptable for a particular corporation.
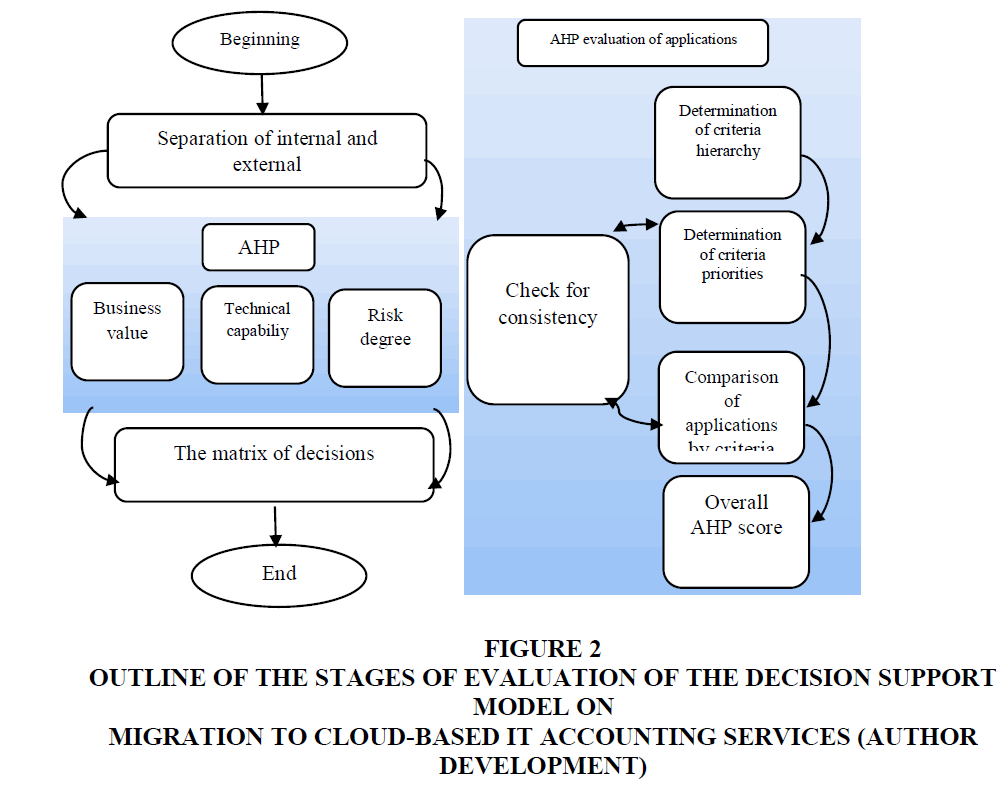
The evaluation of the applications in each of these criteria is a multifactorial analysis of the solutions. Figure 2 demonstrates the steps of evaluation in the form of a scheme based on AHP - Analytic Hierarchy Process.
Figure 2 Outline of the Stages of Evaluation of the Decision Support Model on Migration to Cloud-Based it Accounting Services (Author Development)
First of all, applications that are not clearly suitable for cloud work, such as those that are unable to accomplish tasks in the cloud or that have special security requirements, shall be excluded from the evaluation process from the outset. This shall be done at the 2nd stage of the proposed methodology (“Performance Evaluation”) according to the Integral Model. Applications that have a score less than 0.5 shall be excluded.
In the first stage, the division of applications into internal and external shall be performed. These types of applications shall be evaluated separately because they have different nature and purpose. Internal applications are applications that are accessible only within the corporation and are protected by a firewall; you can also access external applications bypassing the firewall. The argument that each type of application deserves special consideration is the fact that security issues are much more relevant to external applications than to internal applications.
In the second stage, the expert evaluation of the applications is carried out in the context of three criteria. Each of the criteria presented (business value, technical capability and degree of risk) has several sub-criteria; they can in turn have several levels of sub criteria. It is important to take into account the different impact of level sub-criteria, i.e. their weight (significance).
It is suggested to use the hierarchy analysis method to formalize the expertise and calculate the expert evaluations. The method of analysis of hierarchies allows you to consider the hierarchy of criteria by level, to compare criteria based on pairwise comparisons, as well as to formalize both quantitative and qualitative expert information.
A criteria hierarchy is developed for each group criterion proposed.
In the third stage, after performing the AHP assessment, the calculated scores of applications are converted into linguistic assessments. The status "high" is assigned to an application if its score (Sx)> 1/n, where n is the number of evaluated applications. If the score (Sx) <1/n, a status "low” should be assigned.
Then, according to the matrix of decisions (Table 2), the recommendations are formed concerning the choice of cloud IT-services for introduction. Applications that are included into a top line of the matrix will be more suitable for deployment in the cloud environment.
| Table 2 An Example of a Decision Matrix for Applications for Cloud Migration | |||
| AHP evaluation Business value |
AHP evaluation Technical capability |
AHP evaluation Risk degree |
Suitability |
| High | High | Low | Fits all criteria. The applications in this group are best for deployment of migration to the cloud |
| High | Low | Low | Fits two criteria. The applications in this group are suitable for cloud computing |
| Low | High | Low | Fits two criteria |
| Low | Low | Low | Fits one criterion. The applications in this group are not ideal candidates |
| Low | Low | High | Not suitable for any criteria. It is best to leave these applications of this group unchanged |
For example, if 4 applications are rated, then applications with a score greater than 0.25 will have a high status; from 0.167 to 0.25 - "medium"; less than 0.167 - "low".
Recommendations
The potential breaches in information safety are a fundamental major obstacle to implement cloud technologies in the practice of managing administrative processes. The problem with the development of IT-strategy of introduction is that as early as at the stage of its formation it is important to determine which decision support models when choosing cloud IT services for introduction in the corporation will most satisfy the business strategies of the corporation, the compatibility of the existing way of organization of interaction among the subjects of the system in the corporation, evaluate cloud service providers in terms of reliability, trustworsiness, efficiency and security of information flows.
In almost all methods, the basis for determination of the level of risk is the admissibility of an event that determines the level of probability of the threat. The expert method is most often taken as the basis methods of determination of the probability or the statistics data of previous periods are used.
To develop a corporate information security risk management model, you must select a model or combination of models that includes identification, collection, and processing the resultant factors that are inherent in the system and allows you to determine the worst-case scenario for the threat. This model should be adaptive and operationally responsive to the outputs (number of users, number of equipment, data rate, etc.).
So, it is advisable to develop decision support software when choosing cloud-based IT services to deploy them in a corporation using the existing techniques and models discussed in section two.
Conclusion
To make a decision on information safety in the information and computer system of the corporation, namely to manage information safety risks, it is necessary to create a model of formation of information loss risks, namely: to take into account the greatest number of influential factors; allow calculation of the probability of vulnerability and threat implementation; to calculate the time of the threat implementation and possible losses; determine the effectiveness of the implementation of security measures and the degree of security of the system.
Existing methods, models and software products for evaluation of the effectiveness of techniques and determination of the likelihood of implementation of the risks of deployment of IT environment, as well as decision support techniques for choosing cloud-based IT services for introduction in a corporation, were analyzed.
Therefore, the use of a "cloud" version of the accounting program reduces financial and time costs, protects data from loss and third-party interference, eliminates the difficulties associated with updating and IT support. At the same time, there is no difference between the work with a remote version of the program and the regular version of the program, it allows you to perform the same set of functions from any place where there is a computer and Internet access.
As a conclusion, it should be noted that due to the variety of specialized software and the functions that are put to its execution, the software needs to be adapted to the specific conditions of accounting on a specific business entity and is not able to fully reflect its strengths and weaknesses points.
The introduction of ERP technology will make it easier to keep records at enterprises, and will allow to formulate complex management information for management personnel. The digitization, as a process of digitizing accounting information, is an evolutionary step in the development of accounting practices, and is therefore relevant in terms of scientific search and theoretical justification.
References
- Drobyazko S., Barwi?ska-Ma?ajowicz A., ?lusarczyk B., Zavidna L., & Danylovych-Kropyvnytska M. (2019). Innovative entrepreneurship models in the management system of enterprise competitiveness. Journal of Entrepreneurship Education, 22(4).
- Drobyazko S., Shapovalova A., Bielova O., Nazarenko O., & Yunatskyi M. (2019). Formation of hybrid costing system accounting model at the enterprise. Academy of Accounting and Financial Studies Journal, 23(6).
- Hilorme, T., Sokolova, L., Portna, O., Lysiak, L., & Boretskaya, N. (2019). The model of evaluation of the renewable energy resources development under conditions of efficient energy consumption. Proceedings of the 33rd International Business Information Management Association Conference, IBIMA 2019: Education Excellence and Innovation Management through Vision 2020. pp. 7514-7526.
- Hilorme, T., Sokolova, L., Portna, O., Lysiak, L., & Boretskaya, N. (2019). Smart grid concept as a perspective for the development of ukrainian energy platform. IBIMA Business Review, Retrieved from https://ibimapublishing.com/articles/IBIMABR/2019/923814/
- Linthicum, D.S. (2017). Cloud computing changes data integration forever: What's needed right now. IEEE Cloud Computing, 4(3), 50-53.
- Mangiuc, D. (2017). Accountants and the cloud-Involving the professionals. Accounting & Management Information Systems/Contabilitate si Informatica de Gestiune, 16(1).
- Marshall, T.E., & Lambert, S.L. (2018). Cloud-based intelligent accounting applications: Accounting task automation using IBM watson cognitive computing. Journal of Emerging Technologies in Accounting, 15(1), 199-215.
- Neovius, M., & Duncan, B. (2017). Anomaly Detection for Soft Security in Cloud based Auditing of Accounting Systems. In Proceedings of the 7th International Conference on Cloud Computing and Services Science. SciTePress.
- Stancheva-Todorova, E. (2018). How artificial intelligence is challenging accounting profession. Journal of International Scientific Publications "Economy & Business". 12, 126-141.
- Stancheva-Todorova, E. (2019). Using innovative teaching methods in accounting higher education. Journal of International Scientific Publications Educational Alternatives. 17, 104-116.