Research Article: 2022 Vol: 25 Issue: 1
Promoting information security awareness using electronic word-of-mouth through social network sites
Adhi Prasetio, Telkom University
Puspita Kencana Sari, Telkom University
Citation Information: Prasetio, A., & Sari, P. K. (2022). Promoting information security awareness using electronic word-of-mouth through social network sites. Journal of Management Information and Decision Sciences, 25(1), 1-12.
Abstract
Social media provides increased interaction and relationship building between individuals or groups, exercising more influence on their actions and mind-set. Marketing communication organizations already utilize electronic word-of-mouth to build brand awareness effectively. The effect of using these techniques to improve security awareness to protect personal is still understudied. This study aimed to formulate a model that uses electronic word-of-mouth to promote information security awareness, such as brand awareness campaigns in a social media environment. A quantitative methodology with PLS-SEM data analysis techniques was used to analyze questionnaire data research involving 203 social media users in Indonesia. The results showed that source credibility, electronic word-of-mouth quality and quantity, and customer involvement were factors that significantly affected electronic word-of-mouth credibility. Furthermore, electronic word-of-mouth credibility significantly affected information security awareness through its adoption.
Keywords
Adoption model; Electronic word-of-mouth; Information security awareness; Social media.
Introduction
Security breaches that affect individuals come in many forms, including identity theft, malware, gadget theft, and hacking. An example of misusing a Facebook account is a fake account used by irresponsible persons to commit fraud, such as impersonation against others. They typically impersonate other people using photos, identities, and other convincing information from a personal account to gain the trust from a person’s friends list. They manipulate this trust by asking for money by pretending to be in an unfortunate situation and needing help. This kind of attack is called social engineering. Another example is mobile malware attacks. The growth in the number of smartphone users has made them a target of interest for hackers. According to Statista (Statista, 2015), Indonesia is one of the top ten countries suffering from mobile malware attacks, with around 11% of smartphone users in Indonesia infected by mobile malware.
Social media has become an important tool for marketers as it is able to convey one of these marketing modes, called electronic word-of-mouth (eWOM). The immense use of social media contributes to the importance of this platform for marketers. Various marketing studies (Xu & Chan, 2010; Jalilvand & Samiei, 2012; Shojaee & bin Azman, 2013; Charo et al., 2015; Trawnih et al., 2021) have investigated the importance of social media and eWOM. (Charo et al., 2015) study showed how the adoption of online information among Facebook users affects brand image and purchase intention. (Shojaee & bin Azman, 2013) and (Xu & Chan, 2010) also found that eWOM correlates positively with brand awareness and repurchase intention (Ria & Ariyanti, 2017). Since eWOM can be used to increase awareness, information security (Infosec) awareness can also use eWOM to achieve similar results. Social media can be used to promote online information adoption, develop data security awareness, and the desire to protect their details. Information management theory mentions several techniques used widely to increase security awareness inside a company. Nevertheless, the effect of using these techniques to improve security awareness to protect personal information has not been tested.
This research aimed to investigate the role of eWOM in promoting Infosec awareness. Therefore, the following research questions were addressed in this study: (1) what factors are affecting eWOM adoption in social network sites regarding information security? (2) does eWOM adoption on social network sites affect users’ Infosec awareness? To answer those research questions, this study distributed a survey to Indonesian social media users. According to (Salamzadeh, 2020), theoretical contribution of this study includes examining a previously tested theory in a new context and investigating a new relationship among different concepts. This study examines the Elaboration Likelihood Model used for eWOM Adoption (Fan et al., 2013) in marketing context to address research problem in information security awareness context. Practical contribution, especially in Indonesia, was to provide new ways to support cyber security awareness programs. By finding effective ways to improve Infosec among the social media community, we expect the rate of cybercrime to decrease, especially regarding information protection by individuals. The effective implementation of controls in security relies on the environment that has a positive attitude toward safety, encouraging everyone to understand and be involved in behaviors that are expected, such as Infosec (Kruger & Kearney, 2006).
This paper is organized into four following sections. The first section will discuss some literature about information security awareness, electronic word of mouth, and hypotheses development. The second section will discuss the methodology, including the sampling design and data analysis technique. The next section will discuss the result in detail. The last section will define implications and limitations of this study and propose future works.
Literature Review
Security Education Training and Awareness (SETA) is a crucial security control toolkit. It describes a control or rule designed to suppress the incidence of Infosec breaches caused by negligence or planned acts of ignorance (Whitman & Mattord, 2019). The main goal of Infosec awareness is to ensure that system users are aware of the risks associated with the use of the technology and understand the relevant policies and procedures (Kruger & Kearney, 2006). The owner of the system must run programs to improve the Infosec awareness as part of the management of information systems. They are responsible for providing qualified knowledge about the general level of control that is used to ensure all the users that the system is secure (Peltier, 2014). To measure the effectiveness of Infosec awareness programs, the system owner can refer to its stage. There are three components that should be used to measure the Infosec awareness stage: “what users know” or their knowledge; “how they feel about the topic” or their attitude; and “what they do” or their behavior (Kruger & Kearney, 2006).
System owners can use various methods to improve Infosec awareness among users. These methods include education, email messaging, presentations, newsletter articles, computer- based training, video games, group discussions, and posters. Previous studies (Khan et al., 2011) considered that the most effective method is a group discussion because it meets all the criteria in measuring the effectiveness of its methods, such as the knowledge component, subjective norms, intentions, changes in attitude, and behavioral changes. A group discussion is an informal gathering that facilitates many-to-many communication where each member in the group can benefit from exchanging knowledge and experience (Khan et al., 2011). The nature of this method is like a discussion in a community where members can give and receive information on a given review (knowledge) and testimonials (based on experience). This kind of relationship is also known as word-of-mouth. If this conversation happens in electronic media, then it is called eWOM.
eWOM has become popular along with the development of information and communication technology and social media. Moghadamzadeh (Moghadamzadeh et al., 2020) proposed that businesses use social media platforms to engage with consumers in advance and make necessary improvements to their present services. The role of the internet and social media supporting business is arguably becoming more and more important, especially to convey and grab a variety of information, such as in marketing communication. eWOM refers to any statement shared by consumers using internet services, like websites, social networks, instant messaging, news feeds, etc. Such a statement usually contains information about the product, service, brand, or company itself. Marketers can use eWOM to reduce advertising costs by triggering conversations on social media. They can use online influencers or opinion leaders to amplify their messages effectively. The use of eWOM has many advantages since any information shared by a person who is independent (an influencer who has no relationship with the product owner) is more trusted by the audience. They are more reliable because they have no conflicts of interest, especially from those who have credibility to their audience. For this reason, marketing messages conveyed by eWOM are more effective than conventional advertising (Jansen et al., 2009).
The first eWOM variable is source credibility derived from (Wathen & Burkell, 2002). Their research indicated that source credibility is a key aspect in supporting someone to evaluate online information. After online consumers rate the credibility of the medium based on its appearance characteristics, they will rate the source regarding the message content, since source credibility is consistent with trustworthiness and expertise. The following process involves assessing the interaction of the message presentation and the content with the consumer’s cognitive state based on the consumer’s experience and acknowledgment. The online environment changes the nature of the interaction during commerce activities. Buyers rarely touch or feel the product or recognize the eWOM sources. Source credibility is a crucial antecedent in the early phase when a buyer is picking a website, and it contributes to the perceived credibility of messages on the webpage (Dabholkar, 2006; Dou et al., 2012). The buyer’s perceived credibility of eWOM is characterized as the degree to which someone sees a suggestion or audit as believable, true, or factual (Cheung et al., 2009). (Awad & Ragowsky, 2008) proposed that perceived credibility is a prime determinant in a customer's basic decision-making process and improves certainty in both social and business collaborations. According to these arguments, we propose the following hypothesis.
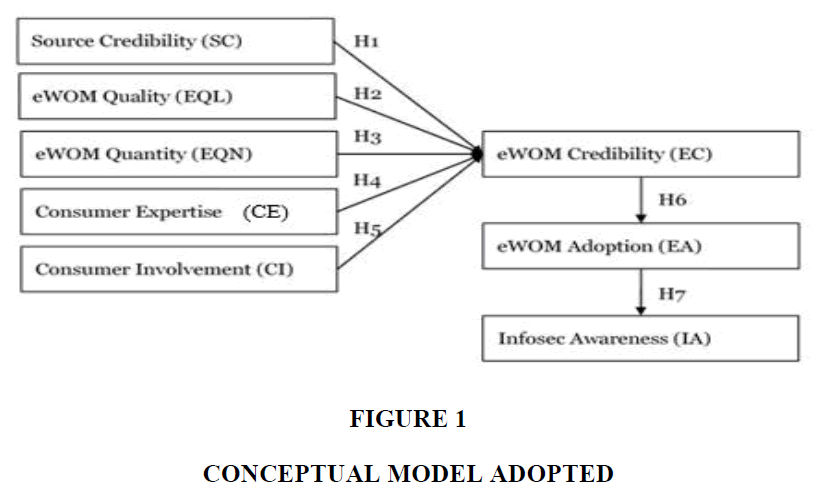
H1: Source Credibility (SC) significantly affects eWOM Credibility (EC).
At the point when a buyer scans for online surveys, the amount of eWOM makes the review progressively recognizable (Cheung & Thadani, 2010); that is, the volume of eWOM reflects the prevalence of an item. Reviewing various comments by others could ease a buyer when settling on a purchase decision since shoppers consider that many other people have bought the same item (Chatterjee, 2001). Some observational examinations (Park et al., 2007; Sher & Lee, 2009) provided proof that eWOM quantity positively impacts the purchaser’s perception of eWOM credibility on low sceptic consumers. According to these arguments, we propose the following hypothesis.
H2: eWOM Quantity (EQN) significantly affects eWOM Credibility (EC).
Electronic WOM quality is another important factor that is normally investigated along with eWOM quantity. When the eWOM on the site picks up customer consideration, buyers start to pass judgment on whether the review deserves further consideration or not. Content quality has been investigated as a significant antecedent of the achievement of an information system (Delone & Mclean, 1992). Consumers consider the accuracy and usefulness of eWOM, and good content quality leads to their readiness to trust (Awad & Ragowsky, 2008). Park et al. (2007) showed that high quality and the amount of eWOM improve persuasiveness. According to these arguments, we propose the following hypothesis.
H3: eWOM Quality (EQL) significantly affects eWOM Credibility (EC).
The Elaboration Likelihood Model (ELM) explains why individuals choose to refer to others’ opinions once creating a buying deal call (Li & Lai, 2014; Park et al., 2007). People who have the intention and are ready to consider a message usually process persuasive messages using the central route. Otherwise, people who lack motivation or ability usually process data by routing them and consult the recommendations of others. In the ELM, involvement is related to the motivation to method data, and experience is related to the flexibility to method data (Petty et al., 1983). Park and Kim (2008) found that customers with high expertise are capable of information evaluation due to their experience and knowledge. Accordingly, (Bansal & Voyer, 2000) implied that such consumers lead to more confidence in making purchase decisions. They also refer less to others’ opinions. We predicted that customer expertise affects the perceived credibility of eWOM and proposed the following hypothesis:
H4: Consumer Expertise (CE) significantly affects eWOM Credibility (EC).
Another important aspect of the ELM is involvement. (Celsi & Olson, 1988) indicated that involvement can be either situational or permanent. Situational involvement is a temporary raise of relevance concerning a product during the purchase decision-making development. We used situational involvement as a predictor for eWOM credibility in this study. Consumers who have higher participation have more enthusiasm to understand products they are interested in and are more likely to read others’ opinions to collect more information, than further effect their purchase behaviour (Ebrahimi et al., 2021). Therefore, we proposed the following hypothesis:
H5: Consumer Involvement (CI) significantly affects eWOM Credibility (EC).
Another study by Fan et al. (Fan et al., 2013) found that eWOM credibility affects eWOM adoption. Their model offers variables to measure eWOM credibility by considering source credibility, eWOM quantity, eWOM quality, consumer expertise, and consumer involvement.
H6: eWOM Credibility (EC) significantly affects eWOM Adoption (EA).
The use of eWOM has been mentioned by Kotler and Keller (Kotler & Keller, 2016) as part of integrated marketing communication modes and found to have a positive correlation with brand awareness, as investigated by Xu and Chan (Xu & Chan, 2010). Infosec awareness has an objective similar to brand awareness, which is making something noticeable by targeted persons. In building brand awareness, organizations mean to make their customers aware of their service or product. Meanwhile, Infosec awareness intends to make their employees or stakeholders aware of their security policy and programs. Therefore, we proposed the following hypothesis based on this description:
H7: eWOM Adoption (EA) significantly affects Information Security Awareness (ISA).
The measurement for eWOM adoption levels was adopted from (Fan et al., 2013), while measurement for Infosec awareness was adopted from (Kruger & Kearney, 2006). The model is adopted from (Fan et al., 2013) by adding Infosec awareness. (Khan et al., 2011) considered that the most effective method is group discussion, which is like a discussion in an online community where members can gain information through eWOM on a given review and testimonials, adopt it, and share it. As eWOM affects awareness in marketing, such as brand awareness (Severi et al., 2014), we replaced brand awareness with Infosec awareness to investigate the direct influence of eWOM adoption on Infosec awareness. Taken from the original model, eWOM adoption is influenced by perceived eWOM credibility, and eWOM credibility is affected by source credibility, eWOM quantity, eWOM quality, consumer expertise, and consumer involvement (Fan et al., 2013). On the other end, the knowledge, attitude, and behavior of consumers measure Infosec awareness (Kruger & Kearney, 2006). Moreover, this study used social media users that were influenced by eWOM adoption instead of consumers in the original research. This research framework can be seen in Figure 1.
Methodology
This research used a quantitative method. Data were collected using a questionnaire and analyzed using Partially Least Square Structural Equation Modelling (PLS-SEM) techniques. The measurement for Information Security Awareness is adopted from (Kruger & Kearney, 2006) with three sub-variables namely Knowledge, Attitude, and Behavior. eWOM measurement is adopted from (Fan et al., 2013) with seven sub-variables Source Credibility, eWOM Quantity, eWOM Quality, Consumer Expertise, Consumer Involvement, Perceived eWOM Credibility, and eWOM Adoption.
Data were collected by sending questionnaires to respondents using an online survey service provider. The population used in this study was social media users who have been exposed to eWOM. This population must have read and received information about Infosec via several means, including threats or protection information campaigns. We used a nonprobability sampling technique. The number of samples collected was 203 respondents.
This research used PLS-SEM to analyze the data. The model of the PLS-SEM consists of the outer model and the inner model. The outer model is assessed using reliability and validity test. Reliability test uses Cronbach’s alpha that reflects the reliability of all indicators in the model. The minimum value is 0.7. Additionally, the value of the composite reliability is used to measure outer model reliability. Composite reliability measures the internal consistency of outer model and the value should be ≥ 0.7 (Fornell & Larcker, 1981; Nunally, 1981; Nunally & Bernstein, 1994).
The validity test in PLS-SEM uses two methods, namely convergent validity and discriminant validity. Convergent validity means that a set of indicators represents one, and only one, latent variable. To measure convergent validity, this research used the value of Average Variance Extracted (AVE). The criteria of AVE value are at least 0.5 (Fornell & Larcker, 1981). Discriminant validity means that the two measured concepts must show adequate difference. The measurement of discriminant validity uses criteria of cross-loadings. When the loading for each indicator is higher than the respective cross-loading, then each indicator meets discriminant validity.
The inner model, also called the structural model, is a model that measures the relationship between latent variables. The measurement of PLS-SEM structural models can be summarized as follows using R2 from each endogenous latent variable: (1) R2 value of 0.67 is categorized as substantial; (2) R2 value of 0.33 is categorized as moderate; and (3) R2 value of 0.19 is categorized as weak. The significance of hypothesis support was determined by using p-values. P-values should be equal to or lower than 0.05 to reject the null hypothesis. The PLS-SEM analysis used in this study was conducted using the WarpPLS software.
Results and Discussion
The measurement model analysis showed that all indicators and variables fulfilled validity and reliability requirements for further analysis. Table 1 shows some related latent variable coefficients. The table indicates that all composite reliability and Cronbach’s alpha values are greater than 0.7. This means that the reliability test was fulfilled. Table 1 also shows the value of AVE for all variables. For convergent validity assessment, all AVE values passed the recommended threshold for acceptable validity 0.5.
| Table 1 Latent Variable Coefficients | ||||||||
| Test Parameter | ISA | EA | EC | SC | EQL | EQN | CE | CI |
| Composite Reliability | 0.948 | 0.964 | 0.900 | 0.949 | 0.903 | 0.940 | 0.944 | 0.909 |
| Cronbach’s Alpha | 0.939 | 0.953 | 0.861 | 0.927 | 0.856 | 0.904 | 0.921 | 0.866 |
| Avg. Variance Extraction | 0.606 | 0.843 | 0.644 | 0.822 | 0.699 | 0.840 | 0.809 | 0.714 |
Table 2 shows the values of R-squared. (Cohen, 1988) mentioned that if the values of R-squared coefficients and adjusted R-squared coefficients are below 0.02, it suggests combined effects of predictors in latent variable blocks that are too weak to be considered relevant from a practical point of view. Since all R-squared value is >0.02, it suggests that all predictors have relevancy to explain predicted variable either in substantial or moderate category.
| Table 2 Measurement Model Test Results | |||
| Test Parameter | ISA | EA | EC |
| R-squared | 0.525 | 0.586 | 0.948 |
| Adj. R-squared | 0.523 | 0.584 | 0.947 |
| Q-squared | 0.528 | 0.585 | 0.761 |
Further results in Table 3 reveal that each latent variable satisfies discriminant validity, since all square roots of the average variance extracted are higher than any of the correlations involving that latent variable (Kock, 2015). Kock mentioned that the following criterion is recommended for discriminant validity assessment “for each latent variable, the square root of the average variance extracted should be higher than any of the correlations involving that latent variable column (Fornell & Larcker, 1981). That is, the values on the diagonal should be higher than any of the values above or below them, in the same column”. Additionally, all the loadings are equal to or greater than 0.5, which also confirmed convergent validity (Hair et al., 1987) Table 4 shows outer loadings results for each indicator.
| Table 3 Correlation Among Latent Variables with Square Roots of AVE | ||||||||
| ISA | EA | EC | SC | EQL | EQN | CE | CI | |
| ISA | 0.779 | 0.724 | 0.590 | 0.411 | 0.420 | 0.331 | 0.202 | 0.460 |
| EA | 0.724 | 0.918 | 0.762 | 0.551 | 0.543 | 0.474 | 0.246 | 0.613 |
| EC | 0.590 | 0.762 | 0.803 | 0.795 | 0.799 | 0.599 | 0.514 | 0.774 |
| SC | 0.411 | 0.551 | 0.795 | 0.907 | 0.788 | 0.636 | 0.581 | 0.705 |
| EQL | 0.420 | 0.543 | 0.799 | 0.788 | 0.836 | 0.732 | 0.611 | 0.740 |
| EQN | 0.331 | 0.474 | 0.599 | 0.636 | 0.732 | 0.916 | 0.601 | 0.636 |
| CE | 0.202 | 0.246 | 0.514 | 0.582 | 0.611 | 0.601 | 0.900 | 0.524 |
| CI | 0.460 | 0.613 | 0.774 | 0.705 | 0.740 | 0.636 | 0.524 | 0.845 |
| Table 4 Outer Loadings | ||||||||
| ISA | EA | EC | SC | EQL | EQN | CE | CI | |
| K1 | (0.809) | -0.529 | 0.211 | 0.162 | -0.298 | 0.168 | -0.071 | -0.037 |
| K2 | (0.803) | -0.477 | 0.206 | 0.149 | -0.327 | 0.209 | -0.047 | -0.054 |
| K3 | (0.826) | -0.371 | 0.156 | 0.100 | -0.307 | 0.215 | -0.065 | 0.006 |
| K4 | (0.754) | -0.154 | -0.099 | -0.035 | -0.107 | 0.356 | -0.161 | 0.010 |
| A1 | (0.869) | 0.248 | -0.456 | 0.045 | 0.089 | 0.085 | -0.067 | 0.062 |
| A2 | (0.849) | 0.308 | -0.439 | -0.029 | 0.061 | 0.037 | -0.030 | 0.186 |
| A3 | (0.854) | 0.246 | -0.219 | -0.189 | 0.330 | -0.124 | -0.011 | 0.090 |
| A4 | (0.832) | 0.145 | -0.109 | 0.054 | 0.085 | -0.131 | 0.043 | -0.051 |
| B1 | (0.594) | 0.017 | 0.551 | 0.093 | -0.107 | -0.299 | 0.164 | -0.166 |
| B2 | (0.832) | 0.067 | 0.045 | 0.010 | 0.091 | -0.107 | 0.053 | -0.087 |
| B3 | (0.625) | 0.327 | 0.278 | -0.474 | 0.418 | -0.349 | 0.260 | -0.049 |
| B5 | (0.627) | 0.248 | 0.186 | 0.043 | 0.132 | -0.250 | 0.038 | 0.026 |
| EA1 | 0.032 | (0.871) | -0.112 | 0.070 | 0.042 | -0.044 | -0.068 | 0.109 |
| EA2 | -0.033 | (0.910) | -0.050 | -0.142 | 0.071 | 0.067 | 0.042 | -0.042 |
| EA3 | 0.007 | (0.952) | 0.036 | 0.006 | -0.070 | 0.098 | -0.075 | -0.027 |
| EA4 | -0.029 | (0.940) | 0.025 | -0.123 | 0.093 | -0.079 | 0.068 | 0.057 |
| EA5 | 0.026 | (0.915) | 0.094 | 0.194 | -0.133 | -0.045 | 0.032 | -0.092 |
| EC1 | -0.068 | 0.322 | (0.846) | -0.160 | 0.030 | -0.287 | 0.096 | 0.046 |
| EC2 | -0.184 | 0.428 | (0.847) | -0.204 | 0.109 | -0.223 | 0.033 | 0.027 |
| EC3 | -0.028 | 0.038 | (0.800) | -0.226 | 0.131 | -0.087 | 0.118 | 0.084 |
| EC4 | 0.155 | -0.602 | (0.725) | 0.155 | -0.249 | 0.431 | -0.112 | -0.126 |
| EC5 | 0.156 | -0.290 | (0.788) | 0.477 | -0.053 | 0.239 | -0.156 | -0.049 |
| SC1 | -0.009 | 0.106 | -0.119 | (0.894) | -0.106 | 0.168 | 0.019 | -0.019 |
| SC2 | -0.011 | 0.085 | -0.098 | (0.937) | 0.144 | -0.188 | 0.003 | -0.070 |
| SC3 | 0.065 | -0.280 | 0.375 | (0.880) | -0.243 | 0.148 | -0.067 | -0.010 |
| SC4 | -0.043 | 0.079 | -0.144 | (0.915) | 0.190 | -0.113 | 0.043 | 0.101 |
| EQL2 | -0.060 | 0.269 | -0.229 | 0.150 | (0.867) | -0.299 | 0.002 | 0.163 |
| EQL3 | 0.020 | 0.179 | -0.116 | 0.298 | (0.821) | -0.162 | -0.037 | -0.218 |
| EQL4 | 0.164 | -0.358 | 0.218 | -0.314 | (0.794) | 0.220 | 0.074 | -0.121 |
| EQL5 | -0.109 | -0.112 | 0.140 | -0.145 | (0.860) | 0.252 | -0.035 | 0.156 |
| EQN1 | -0.050 | -0.010 | 0.015 | 0.000 | -0.065 | (0.906) | -0.074 | 0.143 |
| EQN2 | 0.010 | 0.038 | -0.026 | -0.134 | 0.254 | (0.933) | 0.090 | -0.114 |
| EQN3 | 0.039 | -0.028 | 0.011 | 0.138 | -0.196 | (0.909) | -0.018 | -0.025 |
| CE1 | 0.017 | -0.015 | -0.003 | -0.062 | 0.313 | 0.132 | (0.848) | -0.192 |
| CE2 | -0.018 | 0.019 | 0.004 | -0.159 | 0.121 | -0.088 | (0.930) | -0.038 |
| CE3 | -0.019 | 0.003 | 0.008 | -0.004 | -0.218 | 0.000 | (0.930) | 0.206 |
| CE4 | 0.022 | -0.008 | -0.010 | 0.230 | -0.198 | -0.034 | (0.887) | 0.008 |
| CI2 | 0.032 | 0.129 | -0.241 | 0.221 | 0.149 | -0.087 | -0.098 | (0.882) |
| CI3 | 0.014 | 0.097 | -0.163 | -0.072 | 0.097 | 0.008 | -0.068 | (0.849) |
| CI4 | -0.061 | -0.034 | 0.137 | -0.012 | -0.080 | 0.003 | 0.076 | (0.823) |
| CI5 | (0.809) | -0.529 | 0.211 | 0.162 | -0.298 | 0.168 | -0.071 | -0.037 |
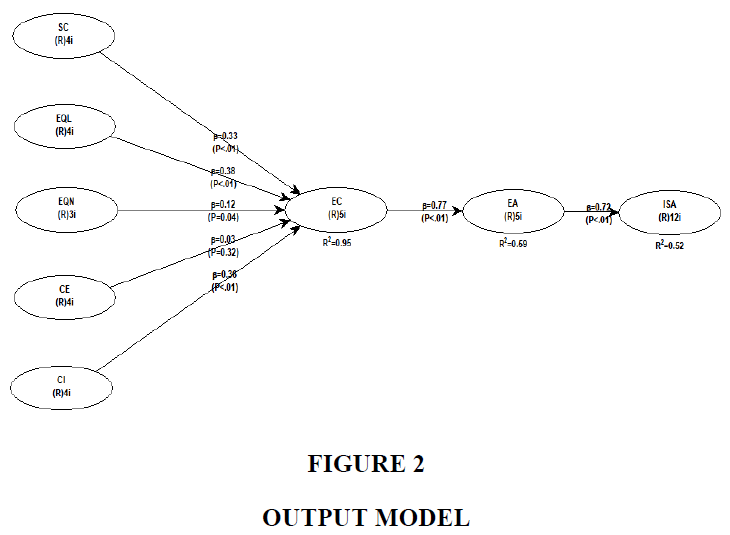
Table 5 summarizes the hypotheses test results. All hypotheses are accepted, except H4. Four variables had different strengths in affecting eWOM credibility. eWOM quality was the strongest variable, followed by customer involvement, source credibility, and eWOM quantity, respectively. Furthermore, eWOM credibility affected eWOM adoption and eWOM adoption affected Infosec awareness. The coefficient determination value of Infosec awareness showed a moderate level, which means it can be predicted by eWOM adoption properly Figure 2.
| Table 5 Hypothesis Testing Results | |||
| Hypothesis | Path coefficient | P-value | Conclusion |
| H1: SC → EC | 0.33 | <0.1 | Supported |
| H2: EQL → EC | 0.38 | <0.1 | Supported |
| H3: EQN → EC | 0.12 | 0.04 | Supported |
| H4: CE → EC | 0.03 | 0.32 | Not Supported |
| H5: CI → EC | 0.36 | <0.1 | Supported |
| H6: EC → EA | 0.77 | <0.1 | Supported |
| H7: EA → ISA | 0.72 | <0.1 | Supported |
The Goodness-of-Fit report results showed that our model was fit enough to explain variables in the model. Table 6 shows the report of each measure.
| Table 6 Goodness-of-Fit Results | |
| Measures | Report |
| APC (avg. path coeff.) | 0.387, P<0.001 |
| ARS (avg. R-squared) | 0.686, P<0.001 |
| AARS (avg. adjusted R-squared) | 0.684, P<0.001 |
| AVIF (avg. block) | 3.224, ideal (<=3.3) |
| AFVIF (avg. full collinearity) | 3.451, acceptable (<=5) |
| GoF (Tenenhaus Goodness of Fit) | 0.716, large (>=0.36) |
| SPR (Sympson’s paradox ration) | 1.000, ideal (=1) |
| RSCR (R-squared contribution ratio) | 1.000, ideal (=1) |
| SSR (Statistical suppression ratio) | 1.000, acceptable (>= 0.7) |
| NLBCDR | 1.000, acceptable (>= 0.7) |
Data analysis results showed four factors affecting eWOM credibility in the context of Infosec campaigns in social media. These factors were source credibility, eWOM quality, eWOM quantity, and customer involvement. The nature of social media makes it hard to confirm source credibility. Users can easily share information and usually do not bother to confirm shared content. This result supported a previous study (Fan et al., 2013) that found that source credibility significantly affects eWOM credibility. Bonding relationships among users could lead to bias when judging source credibility. Users tend to consider their close and trusted relatives within their networks and view them as credible sources, especially when the information comes from a perceived credible group. Verification of online social media source credibility is difficult, but this result showed that online source credibility significantly affected eWOM credibility, as seen in a previous study (Fan et al., 2013).
Prior results (Fan et al., 2013) also showed that customer involvement had no significant effect on eWOM credibility. It was revealed that customer involvement could influence eWOM credibility as well. Respondents seemed to have higher participation and therefore more enthusiasm to understand their interests, such as information regarding to and are more possible to read others’ opinions to collect more information. This could lead to a higher eWOM credibility perception.
eWOM quality and quantity also significantly triggered eWOM credibility. This result was relevant to a previous study (Fan et al., 2013). Respondents considered the accuracy and usefulness of eWOM when they received messages frequently. If they considered the eWOM content to be good quality, it led to their readiness to trust eWOM (Awad & Ragowsky, 2008; Park et al., 2007) and improved persuasiveness. Meanwhile, customer expertise had no effect on eWOM credibility. This result was similar to prior research by (Fan et al., 2013). Intention and readiness to consider a message usually process persuasive using the central route.
As expected, these results also supported previous research by (Fan et al., 2013) that eWOM credibility affects eWOM adoption. Furthermore, still supporting the same study, eWOM adoption will improve information security awareness. This result was similar to the results of a brand awareness study (Shojaee & bin Azman, 2013). Although security awareness and brand awareness are not exactly the same, from this result we could see that eWOM adoption could also significantly impact security awareness.
This study indicated that eWOM is important to encourage sharing of knowledge in online social networking ecosystems. Social network users may want their relatives to have similar benefits that they get, especially when they feel that content has good quality (Sari & Prasetio, 2017) and beneficial for them (Choi & Scott, 2013). Even though this research already answered the research question using structural equation modeling analysis technique, but other rising methodologies could unshed some new ways to understand how information on security awareness is disseminated through social network environment. Those methodologies includes social network modelling approach (Alamsyah et al., 2014) or clustering model based on specific domains and resources (Lubis et al., 2018).
Conclusion
This study’s results showed that four variables influenced eWOM credibility; consist of source credibility, eWOM quantity, eWOM quality, and customer involvement. This research also revealed that eWOM credibility affects its adoption, which furthermore affects information security awareness. For theoretical implication, this research proposed an empirical model that used brand awareness antecedents to improve Infosec awareness. As practical implication, organization can use eWOM techniques as information security education program to improve consumer and employee’s awareness by creating a group discussion to increase their involvement. In addition, organization should consider the quality and quantity of eWOM and also source of information they used.
There are some limitations to this study. First, the respondents were dominated by one age group, with more than 60% of respondents 20-29 years old. Although most social media users are also dominated by that age group, different influences might have been had by other groups. Further research might use a more proportional sample and compare the different effects among those groups. Second, this research did not consider other behaviors that usually follow awareness, such as knowledge sharing. Further study could add the knowledge sharing variable as an additional construct related to eWOM adoption, eWOM credibility, and information security awareness. We suggest that eWOM plays an important role in encouraging the sharing of knowledge, especially in online social networking environments. If social network users feel that content is good quality and beneficial, then they may want their relatives to have the same benefits. Further research could also use other methodologies to understand how information on security awareness is disseminated, using the social network modelling approach or clustering model based on specific domains and resources.
References
Charo, N., Sharma, P., Shaikh, S., Haseeb, A., & Sufya, M. Z. (2015). Determining the Impact of Ewom on Brand Image and Purchase Intention through Adoption of Online Opinions. International Journal of Humanities and Management Sciences, 3(1), 41-46.
Cheung, C. M., & Thadani, D. R. (2010). The Effectiveness of Electronic Word-of-Mouth Communication: A Literature Analysis. Bled EConference, 329-345.
Cohen, J. (1988). Statistical Power Analysis for the Behavioral Sciences. NJ: Lawence Erlbaum.
Ebrahimi, P., Salamzadeh, A., Gholampour, A., Innovation, T., & Fekete-farkas, M. (2021). Social Networks Marketing and Hungarian Online Consumer Purchase Behavior: The Microeconomics Strategic View Based on IPMA Matrix. Academy of Strategic Management Journal, 20(4), 1-7.
Hair, J. F., Anderson, R., Tatham, R., & Black, W. (1987). Multivariate Data Analysis with Readings Macmillan. New Work.
Kock, N. (2012). WarpPLS 5.0 user manual.
Kotler, P., & Keller, K. L. (2016). Marketing Management. In Pearson Edition Limited.
Lubis, M., Fauzi, R., & Hasibuan, M. A. (2019). Categorization for the Security Awareness Domain and Resource (SADAR) Model in the Organization: A Clustering Statistical Analysis. Journal of Physics: Conference Series, 1235(1), 012041).
Nunally, J. C. (1981). Psychometric theory. McGraw-Hill.
Nunally, J. C., & Bernstein, I. H. (1994). Psychometric theory. McGraw-Hill.
Peltier, T. R. (2014). Information Security Fundamentals (2nd ed.). Routledge.
Ria, A., & Ariyanti, M. (2017). The Effect of Electronic Word of Mouth, Brand Image, Customer Trust and Customer Satisfaction towards Repurchase Intention at PT. GO-JEK Indonesia. International Journal of Science and Research, 6(7), 1732-1737.
Salamzadeh, A. (2020). What Constitutes a Theoretical Contribution? Journal of Organizational Culture, Communications and Conflicts, 24(1), 1-2.
Severi, E., Ling, K. C., & Nasermoadeli, A. (2014). The impacts of electronic word of mouth on brand equity in the context of social media. International Journal of Business and Management, 9(8), 84-96.
Whitman, M. E., & Mattord, H. J. (2019). Management of Information Security (6th ed.). Cengage Learning.